OUR COMPREHENSIVE
OFFERINGS
That Drive Success
From web development to cloud solutions, we deliver end-to-end digital services that transform businesses and accelerate growth in the digital age.
Core Offerings
Our comprehensive suite of services is designed to meet all your digital transformation needs
PRODUCT DESIGN & DEVELOPMENT
End-to-end product design and custom software development for web, mobile, and enterprise applications, ensuring scalable and user-friendly solutions.
DEVOPS (DEVELOPMENT & OPERATIONS)
Accelerate delivery with our DevOps expertise—cloud migration, CI/CD pipelines, automation, and infrastructure management for seamless operations.
Offensive Security Testing
Identify, assess, and mitigate vulnerabilities with advanced Offensive Security Testing services to strengthen cybersecurity posture and ensure compliance with global security standards.
Testing & Infrastructure Support
Comprehensive manual and automated testing, penetration testing, and performance optimization, combined with proactive application maintenance, bug fixing, and infrastructure management to ensure reliability and business continuity.
Consulting Services
Expert consulting on Agile/Scrum, cloud strategy, data security, and blockchain technology to guide your digital transformation journey.
Our Technology Stack
We leverage the Cutting-Edge Technologies and frameworks to deliver robust and scalable solutions
Web Development
eCommerce Frameworks (Magento, OpenCart, WordPress, CodeIgniter etc.)
System Software
SNMP Manager, Agents, MIB Compiler, MIB Instrumentation
DevOps
AWS, Azure, Google Cloud
Open Source
Information Security
Java, .NET, Payment Transaction Security
Mobility
.NET, Bluetooth, GPS, Cross-platform development
AI/ML
Google Home, Advanced AI Solutions
Blockchain
Supply chain implementations, Fabric development
Ready to Transform Your Business?
Let's discuss how our innovative solutions can drive growth and efficiency for your organization.
Our Process
We follow a proven methodologies like Agile & Scrum that ensures successful project delivery and client satisfaction.
Requirement Gathering
We begin by capturing your goals and requirements with precision, ensuring clear alignment with your business objectives.
Planning & Design
Our experts design scalable, secure, and user-friendly solutions, creating prototypes and architecture tailored to your needs.
Development & Testing
Using modern technologies and industry best practices, we deliver robust solutions backed by manual, automated, and penetration testing for maximum reliability.
Deployment & Maintenance
We ensure a smooth launch, followed by proactive application support, performance tuning, and infrastructure management for long-term success.
Why Choose Us
We combine technical expertise with business acumen to deliver solutions that drive real results.
Proven Expertise
30+ years of global experience in mobility, information security, networking, telecom, web technologies, delivering scalable and secure IT solutions and Enterprise Product Development.
Quality & Timely Delivery
Strong project management, close monitoring, and well-defined processes ensure every solution is delivered on time without compromising quality.
Customer-First Approach
Our mission is to maximize ROI by designing flexible, robust, and tailored IT solutions that meet unique client needs.
Our Products
Discover our innovative products that deliver cutting-edge solutions across security, biometrics, legal tech, and cybersecurity domains.

baiMobile Smartcard Reader
Advanced Smartcard Middleware Framework for Android & iOS applications, providing secure authentication and transaction capabilities with enterprise-grade security.

MBX-ID Access Badge
Fingerprint based Access Control Card for Physical & Logical Access, combining biometric security with traditional access systems for comprehensive protection.
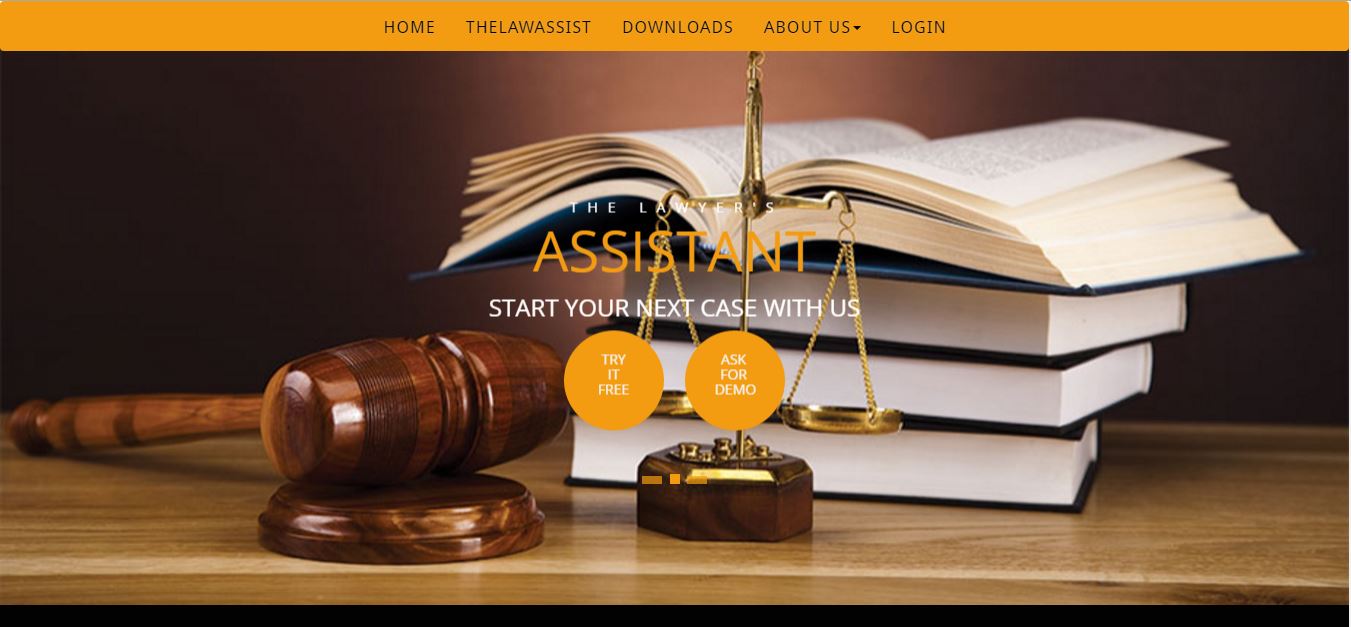
TheLawAssist
Comprehensive legal assistance platform for streamlined case management, client communication, and legal workflow automation designed for modern law firms.

Digitus Egis
Advanced Host Intrusion Detection & Threat Monitoring - Real-time host monitoring, anomaly detection, and automated response to stop cyber threats before they escalate.
Ready to Transform Your Business?
Explore our complete range of products and services designed to accelerate your digital transformation journey.